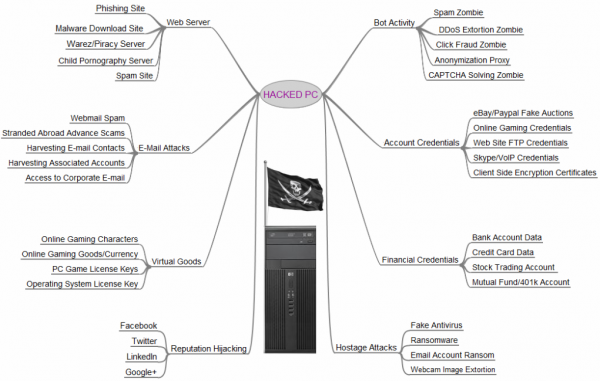
Ransomware is a rather insidious form of malware that attempts to render all of your important files unreadable, until you pay the perpetrator a ransom to restore them. Once paid, you may or may not be given the key needed to restore your files. The best approach to ransomware, by far, is prevention. This article will describe the keys to avoiding ransomware, and will provide advice for what to do if the worst happens.
Source: Ransomware: 7 tips for recovery and prevention
![]()